Function Obfuscation
These are the obfuscation techniques that can be applied to functions. Most of your obfuscation needs will be met by one or more of these features.
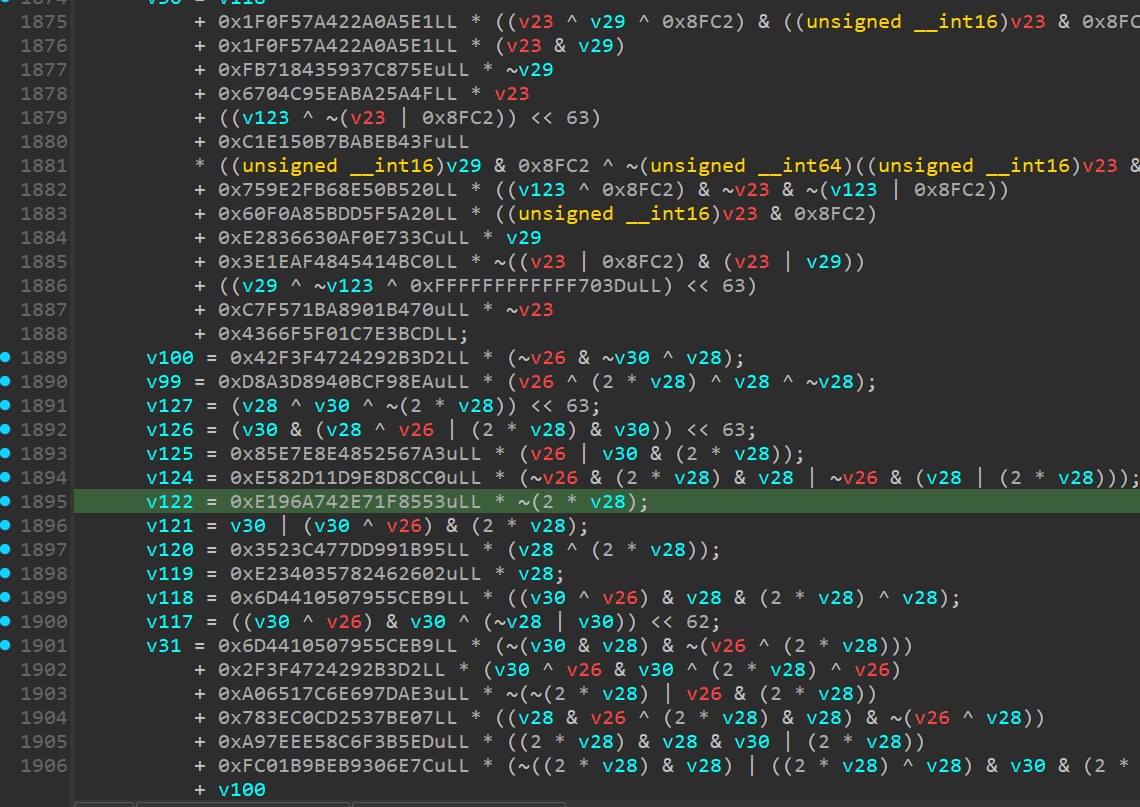
Mutation Engine
This is our proprietary mutation engine, designed to generate intricate expressions using a wide array of x86-64 instructions. It transforms simple instruction sequences into highly complex ones that are so tightly integrated that removing even a single instruction will cause them to fail.
Mixed Boolean Arithmetic
Mixed Boolean Arithmetic pass (MBA).
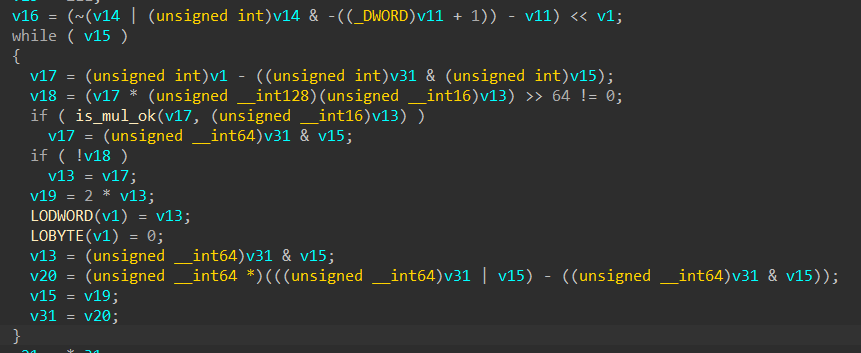
Loop Encode Semantics
This feature takes simple semantics such as Add, Sub, And, and Xor, then encodes their logic as a loop. This confuses symbolic execution engines because the loop bounds are unknown. When combined with other obfuscation techniques, this feature becomes difficult to pattern match and unroll.
Opaque Block Duplication Pass
The opaque block duplication pass duplicates code and creates an opaque predicate to determine which path to take. While this doesn’t significantly reduce efficiency, it will double the function size with each iteration applied.
Dematerialize Constants
This feature obscures constants so they are unlikely to reappear in a register or stack memory location. It is ideal for black-box functions that handle sensitive values. However, if the constant is passed to an external function or written to memory based on the original semantics, it may rematerialize.
Loop-Based Constant Encoding
To enhance security against symbolic execution, constants are encoded using a loop structure. The bounds of this loop are intentionally obscured, making it more challenging for symbolic execution engines to effectively unroll and analyze.
Simple Constant Obfuscation
This feature is designed to evade static signature detection methods, such as locating CRC32 constants by scanning for known values. By obscuring these constant values, the aim is to prevent them from being detected during signature scans. Although this obfuscation technique is relatively weak, it remains challenging to reverse without binary analysis tools.
IDA Decompiler Crasher
This setting effectively breaks IDA Pro's decompiler, preventing any further analysis of the currently open file. It is applied directly to the function you want to shield from decompilation and works across all versions of IDA, including the latest release. To witness the impact, apply the setting to a function, locate it in IDA, press F5, and observe as the decompiler crashes.
An example of the outcome is shown below:
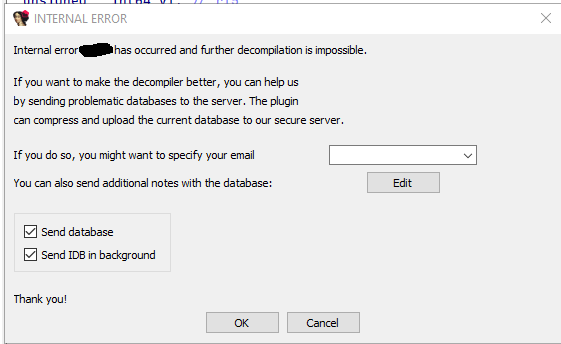
Any further analysis, decompilation, etc., results in this pop-up message: